Research Hacktory Writeup
Hacktory Web security module

Lab Description Link to heading

Let’s try to play spies and find out the secrets of space and time of the Universe Research Laboratory. To do this, we will need a little creativity, logic and attention. In addition to the usual scanning of the root directory, we need to go into the root directory.
Difficulty - 4 shocks out of 5
Solution Link to heading
After starting the car, we read what the bot tells us.
- Bot saying: Use one of the utilities to find the directory with the secret data on http://www.hacktory.lab. Enter the name of this directory
Okay, we’re looking for a directory on www.hacktory.lab
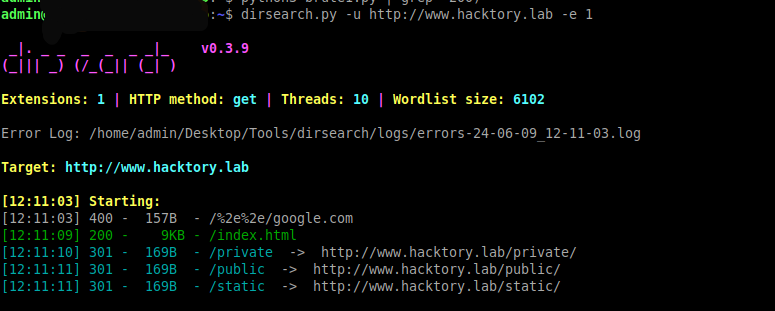
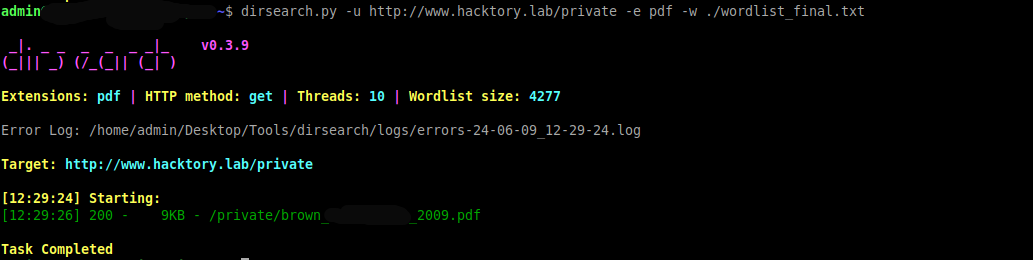
“private” looks suspicious, I think that’s where we’re going.
- Bot saying: So, the directory contains secret research, but unfortunately, the server will return a 403 error when accessing it. Time to get creative. Find a file with publicly available research on the site and write its name.
But the bot says to start with the public. Thinking one step forward, moving two steps back
Let’s look for something in the html markup.
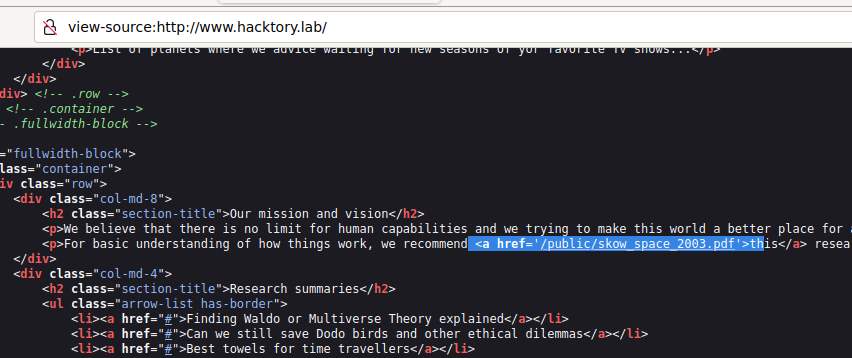
Yeah, there’s a pdf
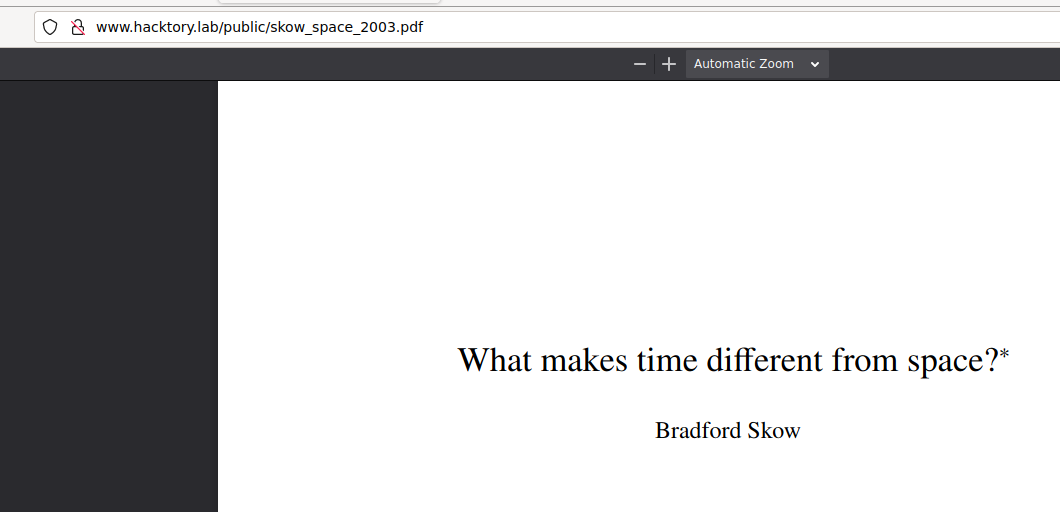
Let’s move on.
- Bot saying: The names of research files on the site are formed according to a certain template. In the private directory there is a file with a secret research and a flag inside. Enter the value of the flag.
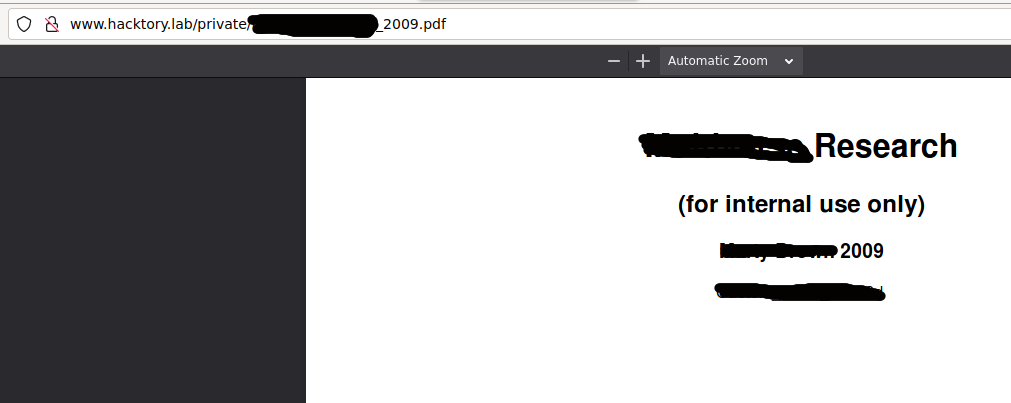
Okay, based on the name of the resulting pdf document, let’s assume that the file name template is surname_word_year.pdf
Using the CeWL utility, let’s create a dictionary based on all the words available on the site. To do this, enter the command cewl www.hacktory.lab -d 3 -m 4 > wordlist.txt
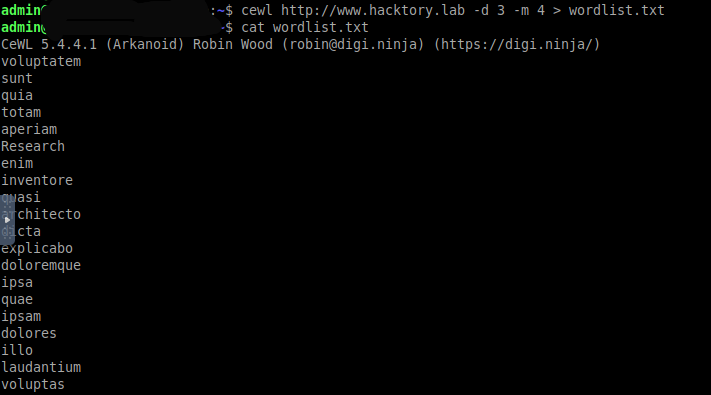
But according to the template, all words in the title should be lower case. They’re not. We need to fix that
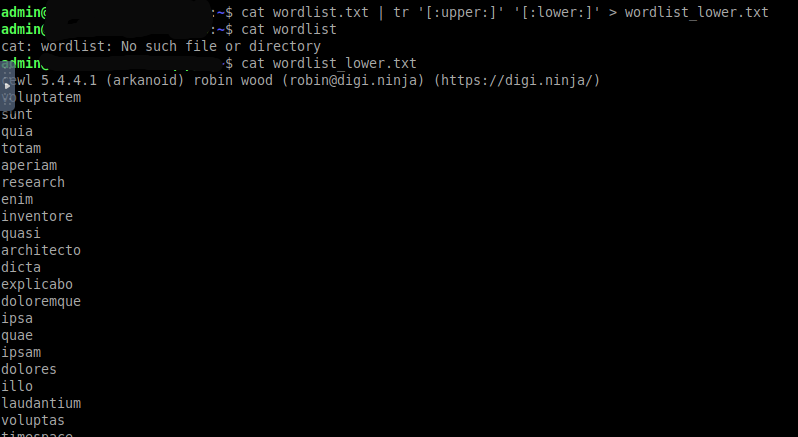
Now that we have a list of all the words on the site ready, let’s look for the researcher’s last name. “Manager” looks promising
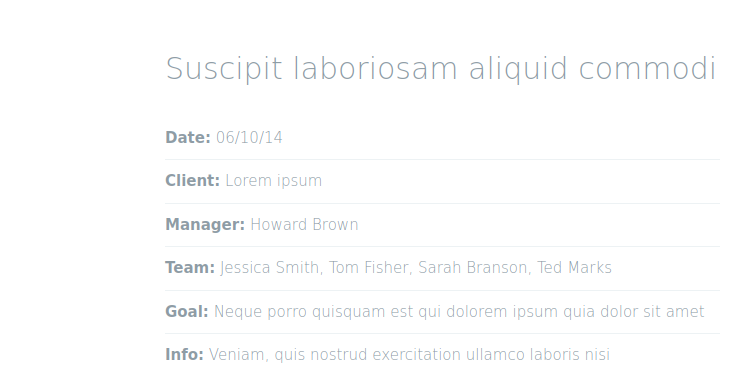
So we have the researcher’s last name, a list of potential titles for his research, and an approximate range of years when that research came out. Let’s generate a dictionary for the brute force attack
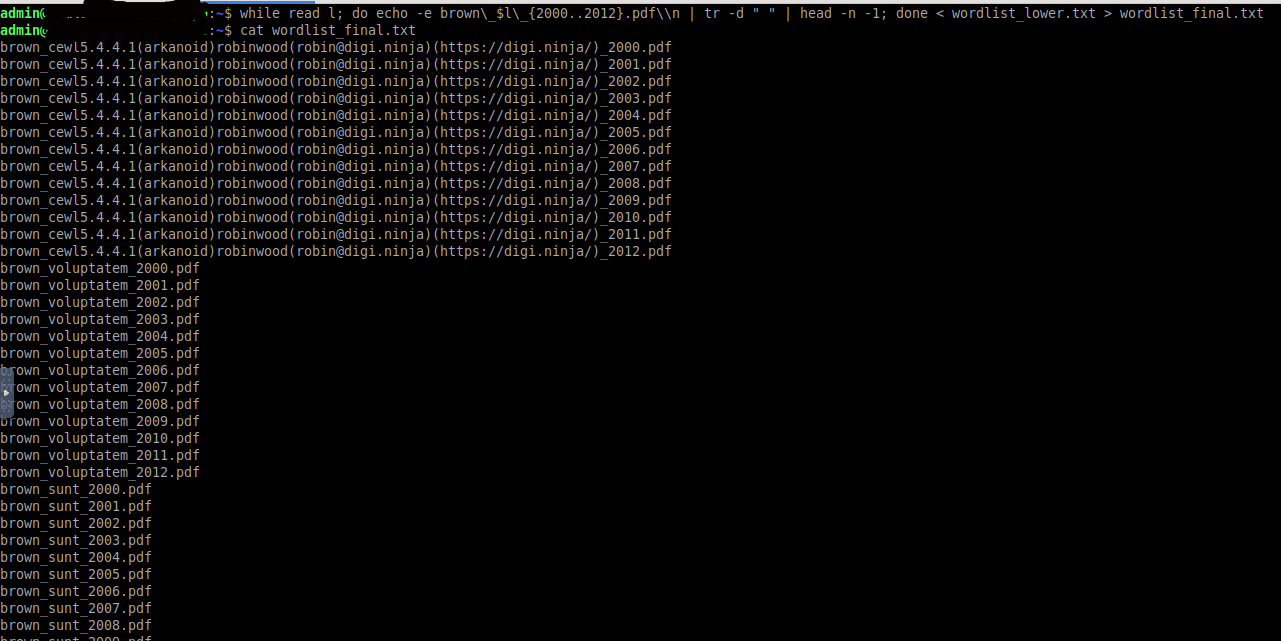
All that remains is to run dirsearch and read the flag in the pdf found